Tips to avoid being tricked by the common cyberattacks hitting schools and workplaces
Even before the pandemic, we were carrying out a huge portion of our day-to-day tasks and work lives online. And since then we’ve shifted even more to doing business within entirely digital environments. But for all the problems this hyperconnected world solves for us, it also means that cybercriminals have increasingly sophisticated means to exploit it. In the financial year, the equivalent of one cyberattack every eight minutes was reported to the Australian Cybersecurity Centre (ASCS).
When a cyberattack is successful, criminals gain illegal access to data stores on a computer or a network. In education environments, such information can be incredibly sensitive, and in the case of ransomware attacks can cost workplaces immense sums of money.
Two forms of cyberattack in particular are on the rise in Australia: phishing – which comes in the form of a disguised email or SMS – and ransomware, malicious software that blocks access to a organisation’s IT system or encrypts its data until a ransom is paid.
Phishing scams are growing exponentially – by 75% during the pandemic, while ransomware attacks rose 15% in 2020-2021. Overall, Australians reported loss of a total of $851 million dollars to scams in 2020 but the number is likely to be far higher.
Phishing: A threat you probably see daily
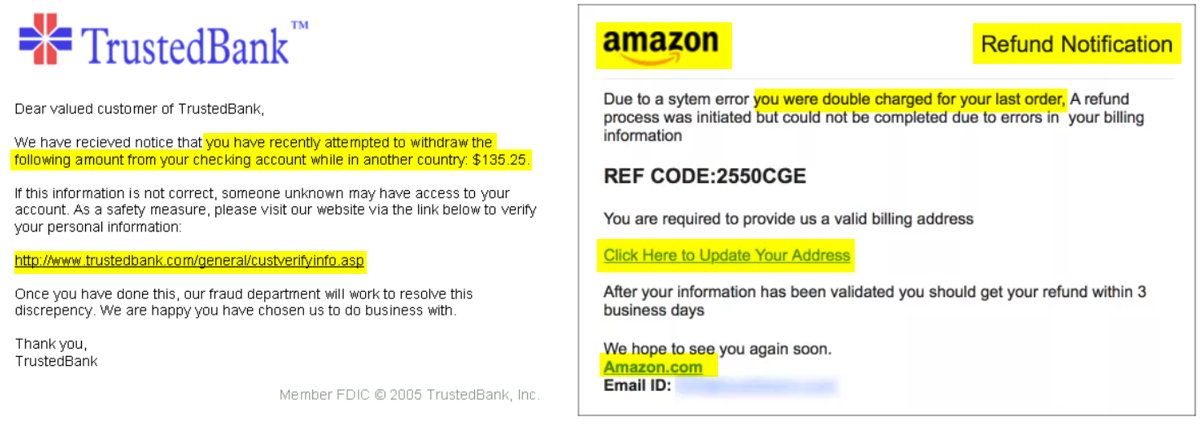
For us day-to-day email users, general phishing attacks have become all too familiar. In these attacks victims receive an email or text message that appears to have been sent by a legitimate institution and convinces the recipient into providing their sensitive data such as personally identifiable information, banking and credit card details, or passwords. Criminals then use this to access accounts and steal identities or money.
Phishing emails have a sense of urgency that criminals have carefully designed to override our common sense. It’s easy to go into work-mode and miss the warning signs. But given what is at stake, it’s wise to get into the habit of treating most unexpected emails as containing a potential threat.
Phishing emails are designed to appear to come from a legitimate source that are common to a lot of us, such as Amazon customer support, a bank, PayPal, your workplace’s software application providers, or other recognised organisation. Cybercriminals hide their presence within the sender’s URL, an email attachment link, and more.
The email will give the impression that you stand to lose something very valuable if you don’t click the link: ‘Someone’s tried to log in to your email’, ‘Your bank has suspended your account’, or ‘Someone just used your Apple ID to order a $500 device’.
Criminals have gotten a lot better at disguising these emails, so that when viewed in a hurry, it’s difficult to tell that they’re fake. The email will be accompanied by a seemingly identical logo to the organisation, as well as its fonts or a legitimate-looking footer.
Examples of requested actions in these emails include clicking an attachment, updating a password or responding to a social media connection request.
Spear phishing: An attack that calls you by name
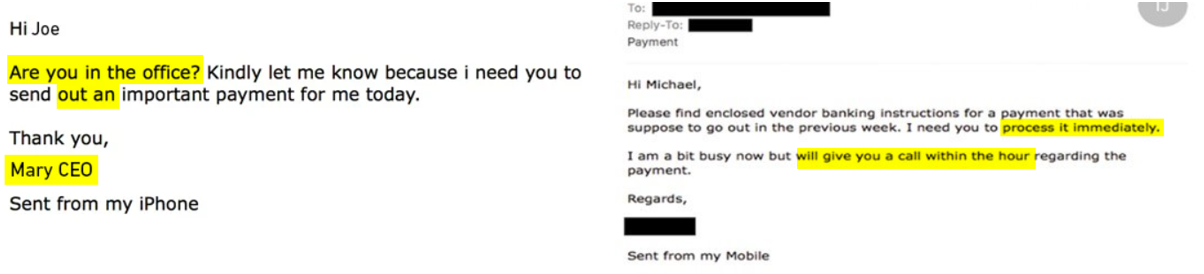
There’s a more sinister form of phishing from which can trick even the most savvy and senior professionals. Spear phishing – which literally, like a spear – is more targeted form of phishing, is on the rise, particularly in the workplace.
It comes in the form of an email or an SMS where a scammer has done their research and found out your name and your manager’s or colleagues’ names and sent you a targeted SMS or email that looks like, and sounds like, it’s coming directly to you from your boss, workmate or a workplace-related supplier or stakeholder.
These attacks can catch us off guard more easily, as they’re designed to trap us in a moment when we are in too much of a hurry or under pressure to think twice about the validity of the message.
The same traits that make them so effective are the exact same first-impression you need to look out for:
- A sense of urgency, that’s usually unexpected or unexplained: ‘I really need your help!’, or “I’ve lost access to my contacts and need you to send me your email / mobile number”.
- The sender is the name of someone you personally know, and their name displays normally in the “From” field.
- The message, while very urgent, will likely be very short and will not contain much detail – rather, it will insist that you need to reply to the person as the action.
Before you hit that Reply button…
Take a moment. Janison’s Head of IT Operations & Security, Garrath Leeds, says it’s the sense of urgency in cyberattacks that catches most people out. He says: They tend to make you feel like you don’t do something quickly for someone you’re going to miss out, you’re going to get in trouble, those sort of things.
“So, my advice when you receive an email asking for urgent action, is to take the time to say “Does this make sense? Is this an email from someone that I think would be sending it to me? Does the request make sense? If it’s someone asking me to click a link to my password, would that happen in real life?”.
Check the actual “from” email address. As you can see in the example, the actual email address itself is not legitimate. The sender name may appear as “Brian Watson” in the From display. But, if the actual email address is not even from your organisation, and instead is a long string of numbers or letters, then you can be confident that it isn’t from “Brian”.
Don’t trust the link. If there’s a link in the email, as a rule of thumb, do not click on it. Links to external websites could allow hackers to access to your school’s or organisation’s entire network or server, or allow remote installation of malicious software that steals the passwords to your bank accounts or other logins.
Visit the sender’s website externally rather than clicking on the link. If you indeed have an account with the “sender”, open a fresh window on your internet browser, navigate to the sender’s main website, and log in safely from there.
Check directly with the sender. Even better, call the sender or the sender’s organisation. The brief time out you take to check “Was this from you?” could save a lot of trouble and potentially financial loss.
Take your passwords seriously
A password is often the only thing between a scammer and your personal records or bank details. Information worth every effort to protect.
Yet, a great majority of us are pretty casual with the way we manage our passwords, even with so much at stake. Passwords that contain our name, place of work or some small variation of a universal personal password that we’ve thought up and use for every single login we have, make the job of scammers much easier.
Ideally, choose a reputable password manager tool to randomly generate and store your passwords, to help enforce robust a barrier between you and cybercriminals.
Switch on multi-factor authentication where possible
Multi-factor authentication (MFA) adds an additional layer of security that requires you to identify yourself through an extra portal – usually a one-time SMS code sent to your phone or email – before you can access an important online account.
It’s important to switch on MFA wherever it’s an option in your security settings, so that there’s a double layer of protection to your password, adding an extra security buffer.
Stay safe in the hyperconnected workplace
Cyberattacks are inevitable. As well as preparing yourself with these tips, keep your IT team informed when you spot a phishing attack, stay across your school’s or organisation’s procedure and details of emergency contacts to report if you’ve been tricked by a malicious link. Reporting an attack immediately can save crucial details being compromised.
About the author
Janison
Unlocking the potential in every learner
You might also like
HRWorkplace ethicsLMSMicrolearningVirtual teamseLearning contentGamified learningWorkplace learningOnboardingInstructional designCoronavirusWHSOnline learningComplianceContent development
Compliance Training Essentials: A Guide to Effective Content That Minimises Risk for Your Organisation [eBook]
Want to learn more about our tailored solutions?
Chat to one of our assessment or learning consultants today.
or call us on 1300 857 687 (Australia) or +61 2 6652 9850 (International)



